
The Rise of Remote Work: Leveraging Managed IT Services for a Seamless Virtual Environment
In the wake of recent global shifts, remote work has emerged as a predominant mode of operation for businesses worldwide. This blog explores the crucial role of Managed IT Services in facilitating a seamless transition to remote work environments, empowering organisations to thrive in this new era of flexibility and connectivity.

Fortifying Defenses: Navigating the Landscape of Cyber Threat Management
Dive into the world of cybersecurity, discussing vulnerability assessments, advanced threat detection, and the importance of a well-defined incident response plan.

Vendor Relationships: A Guide to Effective Vendor Management
This afternoon we discuss the importance of managing relationships with third-party vendors, including SLA monitoring, vendor risk assessments, and effective contract negotiations.

Automation Unleashed: Enhancing Efficiency through Scripting and Automation
Explore the world of automation and scripting, covering script development, process automation, and effective error handling strategies.

Securing the Mobile Frontier: Best Practices in Mobile Device Management
Discuss the challenges and solutions in managing and securing mobile devices, including BYOD policies, mobile app security, and ensuring device compliance.

Seamless Communication: Managing Secure Communication Services
Explore the importance of managed communication services, focusing on unified communications, collaboration tools, and encryption for reliable and secure communication.
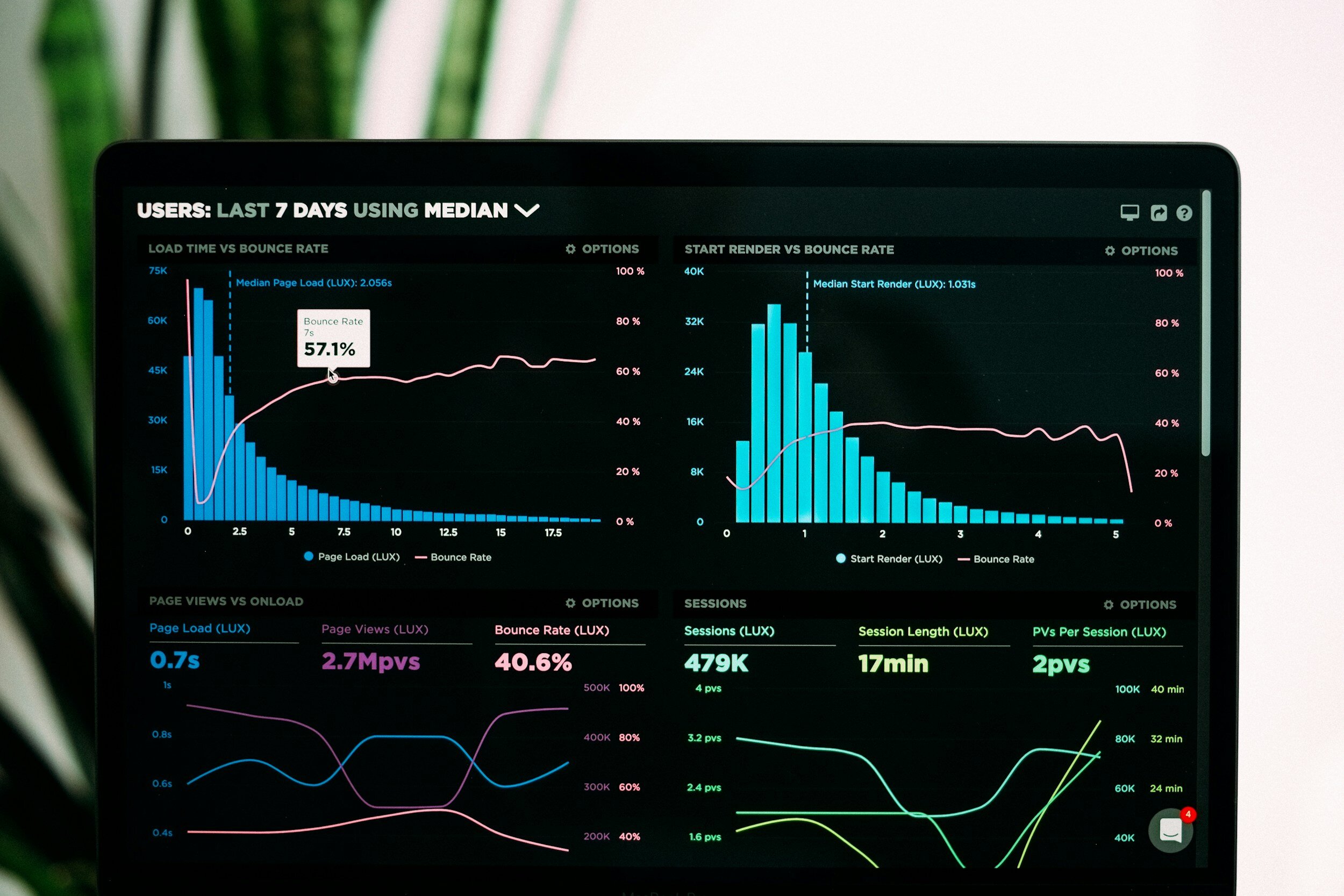
Real-Time Insight: The Power of Monitoring and Performance Optimisation
Discussing the significance of continuous monitoring, performance analysis, and capacity planning in ensuring optimal system performance.

Efficient IT Asset Management: Unlocking Value and Reducing Costs
Explore strategies for tracking and optimising IT resources, touching upon asset tracking, software licensing management, and cost optimisation practices.

Navigating Compliance: A Deep Dive into IT Governance and Regulatory Adherence
Address the importance of compliance and governance, covering aspects like audits, policy enforcement, and maintaining comprehensive documentation.

Empowering Users: Optimising IT Service Desk and Support Operations
Discuss strategies for providing efficient user support, including reducing ticket resolution time, improving user satisfaction, and enhancing knowledge base management.
Securing Endpoints: A Comprehensive Guide to Endpoint Management
Delve into the management and security of end-user devices, focusing on patch management, device monitoring practices, and robust endpoint security measures.

Data Resilience: Strategies for Backup, Recovery, and Testing
Explore best practices for data backup and disaster recovery, covering topics like determining backup frequency, setting recovery time objectives, and establishing effective testing protocols.
